Question 7
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
Correct Answer:A
TheDigital Experience Monitor (DEM)feature in FortiSASE is designed to provideend-to-end network visibilityby monitoring the performance and health of connections between FortiSASE security Points of Presence (PoPs) and specific SaaS applications. This ensures that administrators can identify and troubleshoot issues related to latency, jitter, packet loss, and other network performance metrics that could impact user experience when accessing cloud-based services.
Here??s why the other options are incorrect:
✑ B. It can be used to request a detailed analysis of the endpoint from the FortiGuard team:This is incorrect because DEM focuses on network performance monitoring, not endpoint analysis. Endpoint analysis would typically involve tools like FortiClient or FortiEDR, not DEM.
✑ C. It requires a separate DEM agent to be downloaded from the FortiSASE portal and installed on the endpoint:This is incorrect because DEM operates at the network level and does not require an additional agent to be installed on endpoints.
✑ D. It can help IT and security teams ensure consistent security monitoring for remote users:While DEM indirectly supports security by ensuring optimal network performance, its primary purpose is to monitor and improve the digital experience rather than enforce security policies.
References:
✑ Fortinet FCSS FortiSASE Documentation - Digital Experience Monitoring Overview
✑ FortiSASE Administration Guide - Configuring DEM
================
Question 8
Which secure internet access (SIA) use case minimizes individual endpoint configuration?
Correct Answer:B
Theagentless remote user internet accessuse case is designed to minimize individual endpoint configuration. In this scenario, FortiSASE provides secure internet access without requiring the installation of an agent on the endpoint device. This approach is particularly useful for environments with unmanaged devices or temporary users, as it eliminates the need for complex configurations on each endpoint. Instead, security policies are enforced at the network level, ensuring consistent protection without relying on endpoint-specific software.
Here??s why the other options are incorrect:
✑ A. Site-based remote user internet access:This use case involves securing internet access for users at a specific site or location, typically through a gateway or firewall. While it simplifies configuration for all users at that site, it does not specifically minimize individual endpoint configuration for remote users.
✑ C. SIA for SSL VPN remote users:SSL VPN requires users to connect to the corporate network via a client or browser-based interface. This approach often involves additional configuration on the endpoint, such as installing and configuring the SSL VPN client.
✑ D. SIA using ZTNA:Zero Trust Network Access (ZTNA) focuses on verifying the identity and posture of devices before granting access to resources. While ZTNA enhances security, it may require endpoint agents or posture checks, which involve some level of endpoint configuration.
References:
✑ Fortinet FCSS FortiSASE Documentation - Secure Internet Access (SIA) Use Cases
✑ FortiSASE Administration Guide - Agentless Remote User Access
Question 9
What are two advantages of using zero-trust tags? (Choose two.)
Correct Answer:AB
Zero-trust tags are critical in implementing zero-trust network access (ZTNA) policies. Here are the two key advantages of using zero-trust tags:
✑ Access Control (Allow or Deny):
✑ Determining Security Posture:
References:
✑ FortiOS 7.2 Administration Guide: Provides detailed information on configuring and using zero-trust tags for access control and security posture assessment.
✑ FortiSASE 23.2 Documentation: Explains how zero-trust tags are implemented and used within the FortiSASE environment for enhancing security and compliance.
Question 10
Refer to the exhibits.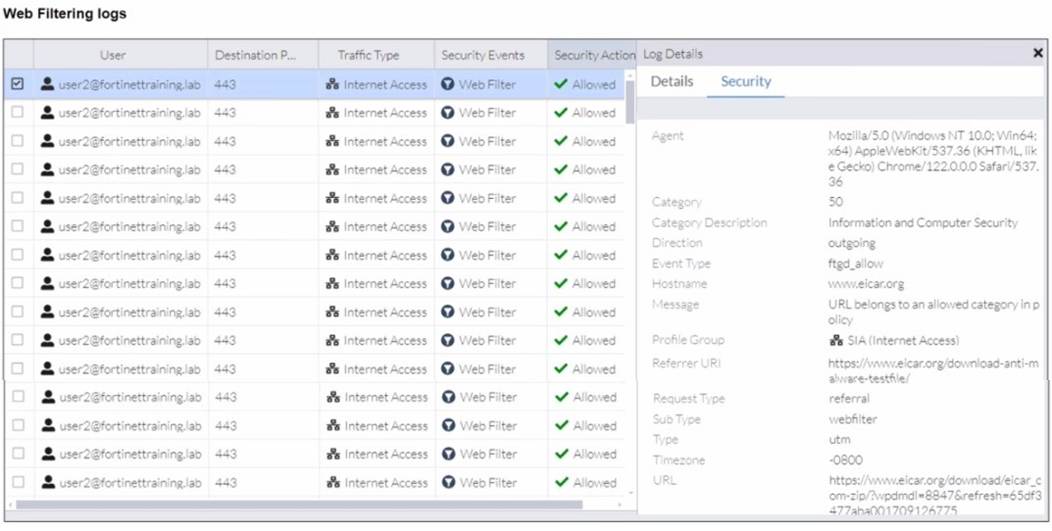
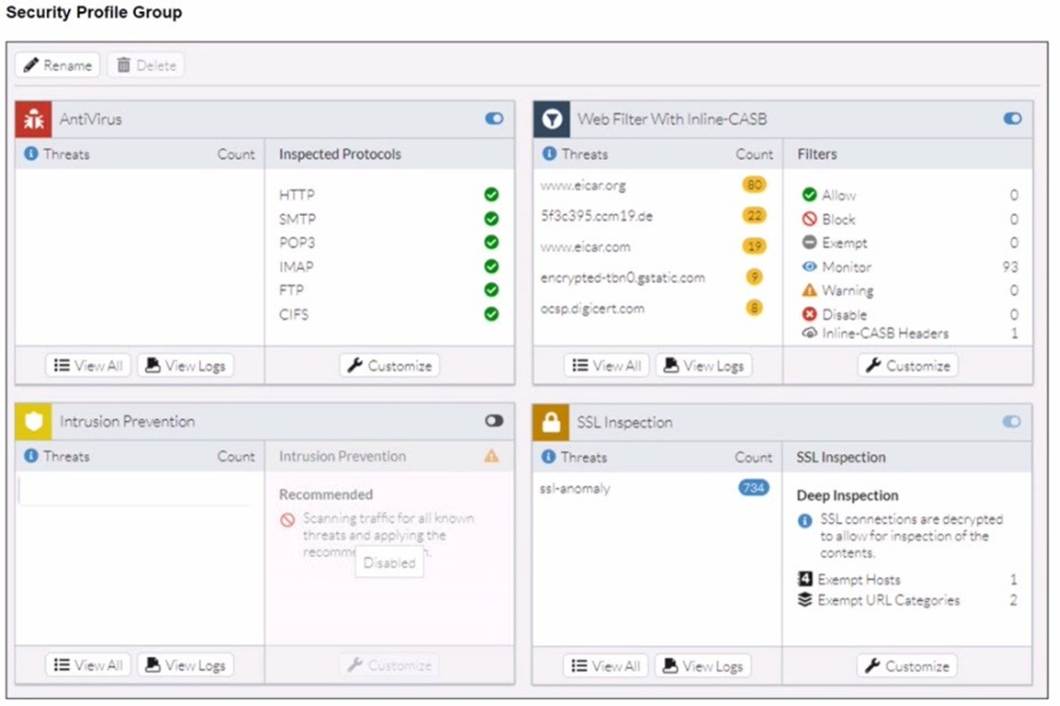
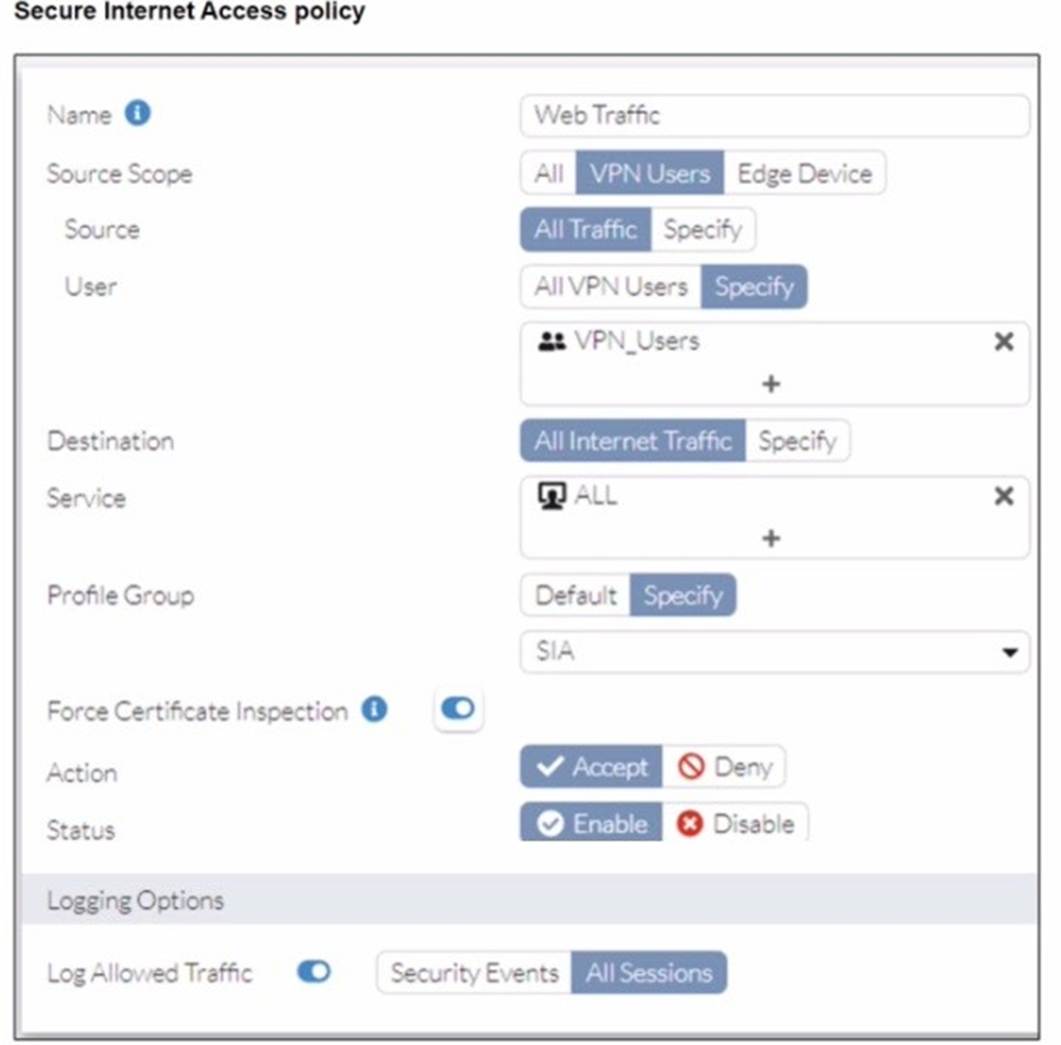
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
Correct Answer:D
https://community.fortinet.com/t5/FortiSASE/Technical-Tip-Force-Certificate- Inspection-option-in-FortiSASE/ta-p/302617
Question 11
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Correct Answer:AB
Onboarding a Secure Web Gateway (SWG) endpoint involves several components to ensure secure and effective integration with FortiSASE. Two key components are the FortiSASE CA certificate and the proxy auto-configuration (PAC) file.
✑ FortiSASE CA Certificate:
✑ Proxy Auto-Configuration (PAC) File:
References:
✑ FortiOS 7.2 Administration Guide: Details on onboarding endpoints and configuring SWG.
✑ FortiSASE 23.2 Documentation: Explains the components required for integrating endpoints with FortiSASE and the process for deploying the CA certificate and PAC file.
Question 12
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
Correct Answer:BCD
References:
✑ FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.
✑ FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate.