Question 7
A local company requires two networks in two new buildings. The addresses used in these networks must be in the private network range.
Which two address ranges should the company use? (Choose 2.) Note: You will receive partial credit for each correct selection.
Correct Answer:AD
The private IP address ranges that are set aside specifically for use within private networks and not routable on the internet are as follows:
✑ Class A: 10.0.0.0 to 10.255.255.255
✑ Class B: 172.16.0.0 to 172.31.255.255
✑ Class C: 192.168.0.0 to 192.168.255.255
These ranges are defined by the Internet Assigned Numbers Authority (IANA) and are used for local communications within a private network123.
Given the options: A. 172.16.0.0 to 172.31.255.255 falls within the Class B private range.
* B. 192.16.0.0 to 192.16.255.255 is not a recognized private IP range. C. 11.0.0.0 to 11.255.255.255 is not a recognized private IP range. D. 192.168.0.0 to 192.168.255.255 falls within the Class C private range.
Therefore, the correct selections that the company should use for their private networks are
A and D. References :=
✑ Reserved IP addresses on Wikipedia
✑ Private IP Addresses in Networking - GeeksforGeeks
✑ Understanding Private IP Ranges, Uses, Benefits, and Warnings
Question 8
A user initiates a trouble ticket stating that an external web page is not loading. You determine that other resources both internal and external are still reachable.
Which command can you use to help locate where the issue is in the network path to the external web page?
Correct Answer:B
The tracert command is used to determine the route taken by packets across an IP network. When a user reports that an external web page is not loading, while other resources are accessible, it suggests there might be an issue at a certain point in the network path to the specific web page. The tracert command helps to diagnose where the breakdown occurs by displaying a list of routers that the packets pass through on their way to the destination. It can identify the network segment where the packets stop progressing, which is valuable for pinpointing where the connectivity issue lies. References := Cisco CCST Networking Certification FAQs – CISCONET Training Solutions, Command Prompt (CMD): 10 network-related commands you should know, Network Troubleshooting Commands Guide: Windows, Mac & Linux - Comparitech, How to Use the Traceroute and Ping Commands to Troubleshoot Network, Network Troubleshooting Techniques: Ping, Traceroute, PathPing.
•tracert Command: This command is used to determine the path packets take to reach a destination. It lists all the hops (routers) along the way and can help identify where the delay or failure occurs.
•ping -t: This command sends continuous ping requests and is useful for determining if a host is reachable but does not provide path information.
•ipconfig /all: This command displays all current TCP/IP network configuration values and can be used to verify network settings but not to trace a network path.
•nslookup: This command queries the DNS to obtain domain name or IP address mapping,
useful for DNS issues but not for tracing network paths. References:
•Microsoft tracert Command: tracert Command Guide
•Troubleshooting Network Issues with tracert: Network Troubleshooting Guide
Question 9
A Cisco PoE switch is shown in the following image. Which type of port will provide both data connectivity and power to an IP phone?
Correct Answer:C
In the provided image of the Cisco PoE switch, the ports identified with number 6 are the standard RJ-45 Ethernet ports typically found on switches that provide both data connectivity and Power over Ethernet (PoE). PoE ports are designed to supply power to devices such as IP phones, wireless access points, and other PoE-enabled devices directly through the Ethernet cable.
Ports:
•2: Console port (for management and configuration)
•3 and 4: Specific function ports (often for management)
•6: RJ-45 Ethernet ports (capable of providing PoE)
•7: SFP ports (for fiber connections, typically do not provide PoE) Thus, the correct answer is C. Ports identified with number 6. References :=
•Cisco Catalyst 2960-L Series Switches Data Sheet
•Cisco PoE Overview
Question 10
Which protocol allows you to securely upload files to another computer on the internet?
Correct Answer:A
SFTP, or Secure File Transfer Protocol, is a protocol that allows for secure file transfer capabilities between networked hosts. It is a secure extension of the File Transfer Protocol (FTP). SFTP encrypts both commands and data, preventing passwords and sensitive information from being transmitted openly over the network. It is typically used for secure file transfers over the internet and is built on the Secure Shell (SSH) protocol1. References :=
•What Is SFTP? (Secure File Transfer Protocol)
•How to Use SFTP to Safely Transfer Files: A Step-by-Step Guide
•Secure File Transfers: Best Practices, Protocols And Tools
The Secure File Transfer Protocol (SFTP) is a secure version of the File Transfer Protocol (FTP) that uses SSH (Secure Shell) to encrypt all commands and data. This ensures that sensitive information, such as usernames, passwords, and files being transferred, are securely transmitted over the network.
•ICMP (Internet Control Message Protocol) is used for network diagnostics and is not designed for file transfer.
•NTP (Network Time Protocol) is used to synchronize clocks between computer systems and is not related to file transfer.
•HTTP (HyperText Transfer Protocol) is used for transmitting web pages over the internet and does not inherently provide secure file transfer capabilities.
Thus, the correct protocol that allows secure uploading of files to another computer on the internet is SFTP.
References :=
•Cisco Learning Network
•SFTP Overview (Cisco)
Question 11
During the data encapsulation process, which OSI layer adds a header that contains MAC addressing information and a trailer used for error checking?
Correct Answer:C
 OSI model
OSI model
During the data encapsulation process, the Data Link layer of the OSI model is responsible for adding a header that contains MAC addressing information and a trailer used for error checking. The header typically includes the source and destination MAC addresses, while the trailer contains a Frame Check Sequence (FCS) which is used for error detection1.
The Data Link layer ensures that messages are delivered to the proper device on a LAN using hardware addresses and translates messages from the Network layer into bits for the Physical layer to transmit. It also controls how data is placed onto the medium and is received from the medium through the physical hardware.
References :=
✑ The OSI Model – The 7 Layers of Networking Explained in Plain English
✑ OSI Model - Network Direction
✑ Which layer adds both header and trailer to the data?
✑ What is OSI Model | 7 Layers Explained - GeeksforGeeks
Question 12
DRAG DROP
Move each protocol from the list on the left to its correct example on the right.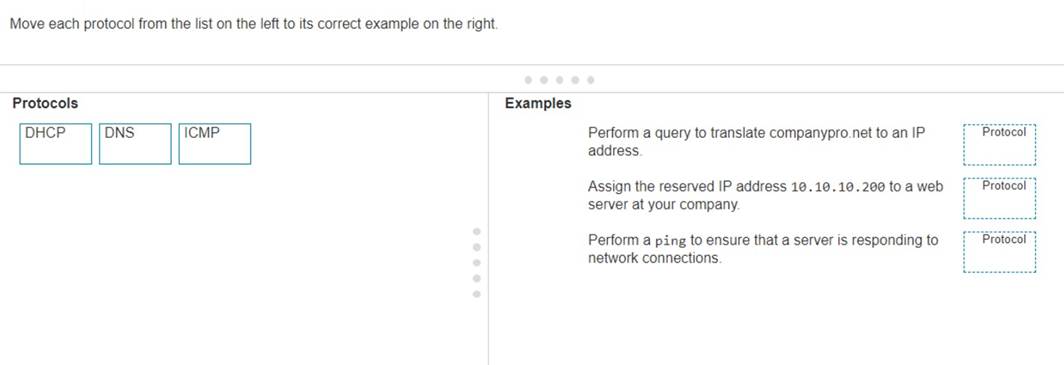
Solution:
The correct matching of the protocols to their examples is as follows:
✑ DHCP: Assign the reserved IP address 10.10.10.200 to a web server at your company.
✑ DNS: Perform a query to translate companypro.net to an IP address.
✑ ICMP: Perform a ping to ensure that a server is responding to network connections.
Here??s how each protocol corresponds to its example:
✑ DHCP (Dynamic Host Configuration Protocol) is used to assign IP addresses to
devices on a network. In this case, DHCP would be used to assign the reserved IP address 10.10.10.200 to a web server.
✑ DNS (Domain Name System) is used to translate domain names into IP
addresses. Therefore, to translate companypro.net to an IP address, DNS would be utilized.
✑ ICMP (Internet Control Message Protocol) is used for sending error messages and
operational information indicating success or failure when communicating with another IP address. An example of this is using the ping command to check if a server is responding to network connections.
These protocols are essential for the smooth operation of networks and the internet.
✑ Perform a query to translate companypro.net to an IP address.
✑ Assign the reserved IP address 10.10.10.200 to a web server at your company.
✑ Perform a ping to ensure that a server is responding to network connections.
✑ DNS (Domain Name System): DNS translates human-friendly domain names like "companypro.net" into IP addresses that computers use to identify each other on the network.
✑ DHCP (Dynamic Host Configuration Protocol): DHCP automatically assigns IP addresses to devices on a network, ensuring that no two devices have the same IP address.
✑ ICMP (Internet Control Message Protocol): ICMP is used for diagnostic or control
purposes, and the ping command uses ICMP to test the reachability of a host on an IP network.
References:
✑ DNS Basics: What is DNS?
✑ DHCP Overview: What is DHCP?
✑ ICMP and Ping: Understanding ICMP
Does this meet the goal?
Correct Answer:A